How Do I Find My Dns Server?
Short Introduction to DNS (switch to a Long DNS caption)
Devices continued to the Net are assigned unique numbers called IP addresses. You know this site as RouterSecurity.org and its IP address is 216.92.136.xiv. All advice on the Internet is based on these unique numbers, website names and computer names are just a convenience. The system that translates names into the underlying numeric IP addresses is called DNS (Domain Name System) and the computers that exercise the translation are referred to as DNS servers.
DNS Servers are extremely of import. Probably 99% of all advice between ii computers on the Internet, starts with a call to a DNS Server to translate a computer proper name into an IP address.
Malicious DNS servers can do what any malicious translator can exercise - lie to you. For example, they might transport you to a scam re-create of a website. Similar food, you lot should not take DNS servers from a stranger.
You can check a computer or router to see what your DNS servers should be, but the pages below show what they actually are (with the tested web browser). That is, they report the DNS servers your current browser is actually using. We demand tests like these because in that location are four places that DNS servers could have come from: (1) the router a computing device is connected to, (ii) the calculating device itself, (3) VPN customer software running on the calculating device or (4) a web browser configured to use encrypted DNS (DoH or DoT). Then once more, your figurer probably supports a system-broad DNS setting and also DNS settings specific to each wireless network (SSID) and peradventure DNS settings specific to Ethernet connections. Whew.
If one web browser is using encrypted DNS while another, on the same computing device, is not, then expect the tests beneath to show unlike results in each browser. Likewise, if you take two spider web browsers using dissimilar secure DNS providers, expect them to study different results in the tests below. For more on encrypted DNS meet the Encrypted DNS topic on my Defensive Computing Checklist site.
Learn Your Electric current DNS Servers
NOTE: If you are using the Private DNS feature of Android (commencement introduced in version nine) there is no need for any of the testers beneath. Android will always apply the Private DNS servers, even when a VPN is agile. Cheers, Google.
See also a listing of suggested DNS providers.
- DNS Leak Test is sponsored past VPN provider IVPN. Information technology offers a quick standard test and a slower extended examination. Both report the IP address, Hostname, Internet access provider, Urban center and Country for each detected DNS server. The initial screen shows your public IP address and location. (final verified Sept 2021)
- At browserleaks.com/ip you may need to scroll down to see a gray "Run DNS Leak Test" button. Click it. Information technology reports the IP Address, ISP, city and country of the detected DNS servers. It does not report DNS server hostnames. Nice thing about this is that you tin meet both the public IP address and the DNS server IP address(es) right next to each other. The page also shows lots of other useful information. (terminal verified Sept 2021)
- The website dnscheck.tools was created in December 2021 by Reddit user dnschecktool. Initially it reports the ISP of the detected DNS server(s), the Advanced tab has many more than details. No ads. No tracking. On a estimator using OpenDNS, some of the detected DNS server names concluded with strln.cyberspace. The domain belongs to Cisco which owns OpenDNS.
- DNS Leaktest from VPN provider Perfect Privacy reports the IP address, host name, Internet service provider and country for each detected DNS server. It does non report the state or urban center where the DNS server is located. (last verified Sept 2021)
- dnsleak.com is sponsored and operated by Kape Technologies, the company that owns VPN provider Private Internet Access. It reports the IP accost, hostname, urban center/region, country and Internet service provider for each detected DNS server. (last verified Sept 2021)
- DNS Leak Test from VPN provider ExpressVPN reports the IP address, "Provider" and Country for each detected DNS server. It does not report a hostname or city. Note that it always warns that "DNS requests exposed!" which actually means yous are non connected to ExpressVPN. (last verified Sept 2021)
- If y'all are using OpenDNS, y'all can verify this at www.opendns.com/welcome/. Rather than show all detected DNS servers, it merely reports a Aye/NO status on whether OpenDNS is in use. (last verified Sept 2021)
- Cloudflare has a tester page at cloudflare-dns.com/help. A more memorable URL that also works is 1.one.1.1/help. The most important affair these report are "Connected to 1.ane.1.1" which is YES/NO. If you are using Cloudflare, it shows the condition of DNS over HTTPS and DNS over TLS. The "AS Proper name" identifies the Isp of your DNS provider. These pages also test the power of your computer to connect to one.ane.one.one and 1.0.0.one and their IPv6 siblings. Note that these tester pages are simply interested in Cloudflare. When it says that neither DoH nor DoT is beingness used, that means they are not being used with Cloudflare. A spider web browser that is using DoH or DoT with another DNS provider, will be reported as not using DoH or DoT.
As detailed on the suggested DNS providers page, Cloudflare offers three DNS services: unfiltered, malware blocking and Family which blocks both malware and porn.
- Verify that the malware blocking is working at phishing.testcategory.com. If the page displays at all, it is Non working.
- Verify that the porn blocking is working at nudity.testcategory.com. If the page displays at all, it is NOT working.
- Screen shots: If phishing is immune, you lot volition see this page. If phishing is blocked you will meet this in Brave or this if using Opera.
Want more? Cloudflare also provides world wide web.cloudflarestatus.com which reports the overall status of their service. Ironically, if their service is down, it will block their users from seeing this website. You can not access cloudflarestatus.com by IP address. I tried. - NextDNS does not accept a defended tester web page, but their website serves the aforementioned purpose. To examination for NextDNS, go to their website and click on the big blueish button that says "Try it at present". The summit of the resulting page will say: "All good! This device is using NextDNS with this configuration" if NextDNS is being used. If non, the folio will say: "This device is not using NextDNS. This device is currently using xxxxxx as DNS resolver". Notation that both messages are poorly worded. The test does not necessarily apply organization wide, it is only guaranteed for the web browser currently being used. Other browsers on the same system and the OS itself could exist using different DNS providers.
Update. June 14, 2020: Thanks to Reddit, I learned today that NextDNS does take a tester page: exam.nextdns.io. However, I could find no documentation on it. Playing with information technology I found that a condition of "ok" and a protocol of either "DOH" or "DOT" means that the browser/Os is using NextDNS. A status of "unconfigured" means it/they are not using NextNDS. When NextDNS is being used, information technology as well shows your public IP address (client IP) and the IP accost of the NextDNS server. (last verified Sept. 2021)) - If y'all use AdGuard for DNS, their overview page includes a tester and volition ostend/deny the use of their service. It is in the centre of the page, look for "AdGuard DNS servers map" If non using their service, it says "You are currently not using AdGuard DNS" In add-on they have a dedicated tester page that tests both for their DNS service and for other software of theirs. (terminal verified Sept 2021)
- The Mullvad connection check page has four big buttons that are either red or dark-green. One is for DNS. If y'all are non connected to the Mullvad VPN, it volition say that you are leaking DNS servers. However, if y'all are using their Secure DNS service without their VPN, it will show in green and say that DNS is non leaking. Click on the downwards pointing arrow on the DNS button to see the IP address, country and Internet access provider of the detected DNS server(south). (last verified March 2022)
- The Tenta VPN tester reports the IP address, Internet service provider, and the urban center, state and land for detected DNS servers. Information technology does not testify the hostname. If you click the link to the Avant-garde Exam results, then it also shows a whole host of advanced data about each DNS server. The meaning and importance of this information is beyond me (and not explained). The test may exist buggy, I one time saw the same DNS server IP address listed eight times. (last verified Sept 2021)
- ipx.air-conditioning is from VPN provider VPN.air conditioning. Click the big orange push button to "Test for leaks and footprints" at the bottom of the folio to meet the IP accost, country and Isp of detected DNS servers. It does not prove the names of each DNS server. The page tests much more than just DNS. (last verified January. 2022)
- whatsmydnsserver.com is from the people that gave upwards top10vpn.com. It reports the IP address, Internet service provider and State where your DNS server lives. It does not report the DNS server proper noun. The caption of DNS on the page is atrocious. (last verified January. 2022)
- The F-Secure Router Checker does not really bank check routers, it just reports on a DNS server (IP accost, Isp and country). The company says their goal is to insure that your router is using an "authorized DNS server" only there is no such matter and they don't ascertain it. (last verified Sept 2021)
- ipleak.net is from VPN provider AirVPN. For each DNS server, it reports the IP address and location. No ISP or DNS server hostname. It also reports on many other things such every bit WebRTC and your screen resolution. This is my to the lowest degree favorite option as the font used for the IP addresses is all but unreadable. It is too available on ports 8000 and 62222.
OPERATING SYSTEM TESTS
To see what the Operating System is using for DNS, exterior of any spider web browsers, nosotros tin can utilize the nslookup command on desktop operating systems (Windows, macOS, Linux). The command syntax is very simple: "nslookup domainname". The get-go thing returned by the command is the name and IP address of the default DNS server. Below is a screen shot from Windows 7 showing the system is using DNS server dns9.quad9.net at IP address nine.9.ix.nine.
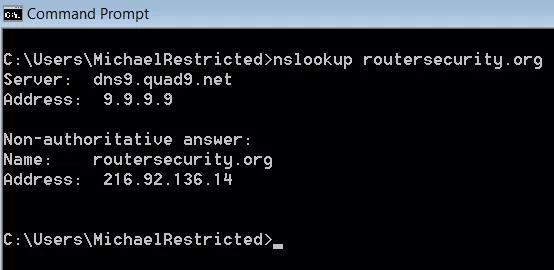
DNS configurations in the Operating Organization tin be all over the map. There can be different DNS servers configured for Ethernet vs. Wi-Fi. And, each wireless network (SSID) can be configured to use different DNS servers. Android 9, ten, 11 and 12 permit a global DNS setting for the entire operating system. iOS is the exact opposite, it fifty-fifty allows each app to configure its ain DNS servers.
If a specific network connectedness does non specify any specific DNS server(s), and then it gets assigned DNS servers past the router. Merely, again, a complexity. The router may function every bit a DNS server itself, or it may simply pass DNS requests out to a DNS server on the Internet.
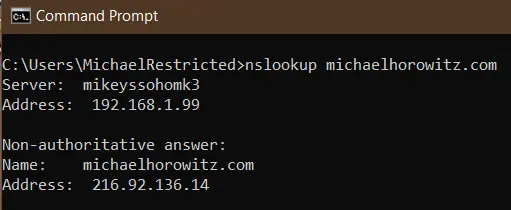
In the example above, the network connection was specifically configured to use Quad9. In the case below, a Windows ten computer is using the router itself (at 192.168.1.99) as the DNS server.
Some other option for Windows users is the ipconfig control. Its equivalent for MacOS and Linux is ifconfig.
On Windows, the command ipconfig /all shows details, including the DNS server(s) for all the divers network connections. When connected to a VPN, there will be one entry for the internet connection without the VPN (WiFi or Ethernet or 4G) and another entry for the VPN connection. Which DNS servers are really being used by the OS when not running a web browser? See nslookup above.
This command tin can also useful after endmost a VPN connection. I have seen VPN software that did not reset the DNS servers correctly when shut down. This left the computer using the DNS servers from the VPN company even when the VPN software was not running.
On both Linux and macOS, you tin use the dig command to see which DNS server is being used. On macOS, do Applications -> Utilities -> Terminal. For Linux see How to Use the dig Command on Linux by Dave McKay (Apr 2020). A simpledigsomedomain.com command should brandish the DNS server used to answer the question. Look for "SERVER:" in the output.
DNS IS COMPLICATED
It is commonly thought that if the Operating Organisation specifies DNS servers (either for Ethernet or for a specific SSID) they volition get used. This is not always the case. Some routers (such as the Pepwave Surf SOHO) tin can force clients to use the DNS servers specified in the router. Worse, if the router is doing this (at least with Peplink routers) the computer tin can non tell. The DNS server the computer sees is not the one really being used.
This means that the DNS server reported by nslookup can not exist trusted. In the first screen shot in a higher place, it looks like Windows is using 9.9.9.nine for DNS resolution. But, if Windows is configured to apply nine.9.9.9 and the router is configured to use ane.1.one.1 (for example) and the router is imposing its will on all the attached devices, nslookup volition report that it is using 9.9.9.9. It is non lying on purpose, it is being faked out by the router. The packets leaving the WAN port of the router will be sent to 1.i.one.1. I learned this the hard style, past doing pcap traces of information packets leaving the WAN port. I assume the same is true with the dig command on Linux and macOS.
That said, my experience has been that a router forcing the use of its DNS servers, only applies to sometime DNS. Browsers that specified DoH or DoT secure DNS servers had their requests honored because, to the router, a secure DNS request is a totally different thing than an old DNS request.
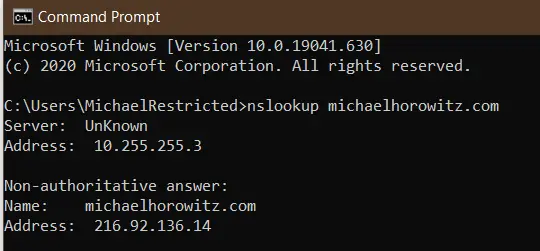
And, of course, a VPN complicates this farther. Below is a screen shot of nslookup done while a Windows 10 computer was connected to a VPN. In this case, nslookup returns the IP address of the DNS server on the internal network of the VPN provider (10.255.255.3). The server is not unknown, but its proper name is.
Windows users tin trace all instances of legacy DNS using two gratuitous and portable programs from Nir Sofer: DNSQuerySniffer (meet a screen shot) and DNSLookupView. Each has its own pros/cons. If y'all run these programs before starting up a browser, you will meet the browser making sometime (not secure) DNS requests to detect the Secure DNS server. If things are working equally they should, the only browser DNS requests, visible to Windows, are those for the Secure DNS server itself. Another idea is to run these programs with nothing going on, and see where Windows is phoning domicile to. I did this in October 2021 and plant Windows 10 logging many deportment in the Organization Settings app. And, you can use DNS to block Windows from being able to log your actions.
Notwithstanding another approach, for Windows, was suggested by Sergiu Gatlan in his August 2020 article Microsoft adds Windows 10 DNS over HTTPS settings section. He suggests using the pktmon command to trace all activity on TCP/IP port 53. The pktmon command can not display simply outgoing requests, information technology always includes the replies besides, so information technology generates a lot of activity in the command window. But, it will confirm the employ of old DNS. The commands Gatlan suggests are:
pktmon filter remove
pktmon filter add -p 53
pktmon start --etw -fifty real-fourth dimension
I suggest commencement doing a pktmon filter listing just to see if any filters are active. The logging tin can be stopped with Ctrl+C.
SAD DNS
A new attack on DNS servers, called Sorry DNS was made public in November 2020. The attack tries to poison the DNS results, that is, pointing victims to a malicious server at the incorrect IP accost for a domain. The attack was created by six academics at the Academy of California, Riverside and at Tsinghua Academy. See their paper and slides.
Yous can examination if you are using a vulnerable DNS server using the "Click to cheque if your DNS server is affected" link on the SAD DNS folio. They warn, notwithstanding, that their test is not 100% accurate.
On November 12, 2020 I ran some tests. Cloudflare, Google and Quad9 were all vulnerable. The DNS from my VPN provider was non. NextDNS initially could not resolve the Lamentable DNS page. The log showed that information technology was blocking saddns.net because it was a newly registered domain. No big deal to white listing the domain. NextDNS was also reported every bit vulnerable.
Why Bother
Hacking a router and changing the DNS servers is a very pop type of assail. Some reports in the news:
- Brazil is at the forefront of a new blazon of router set on by Catalin Cimpanu for ZDNet July 12, 2019
- Website drive-by attacks on routers are alive and well. Hither'south what to do by Dan Goodin July xi, 2019
- NCSC Issues Alert About Active DNS Hijacking Attacks by Ionut Ilascu for Bleemping Computer July 14, 2019
- Ongoing DNS hijackings target Gmail, PayPal, Netflix, banks and more by Dan Goodin of Ars Technica April five, 2019
And...
Alert to Windows users: In that location is a caching or buffering issue involving VPNs. After connecting to a VPN, the to a higher place sites typically evidence both the pre-VPN DNS servers and the current DNS server from the VPN provider. On iOS 12 and Android 7.1 all the higher up testers piece of work fine, only Windows is buggy. I accept not tested other OSs. In the screen shot below, from the Express VPN tester page, the four OpenDNS servers were in utilize before the VPN connection was fabricated and the server at Leaseweb USA is from the VPN provider. I tried the command "ipconfig /flushdns" simply it did non help.
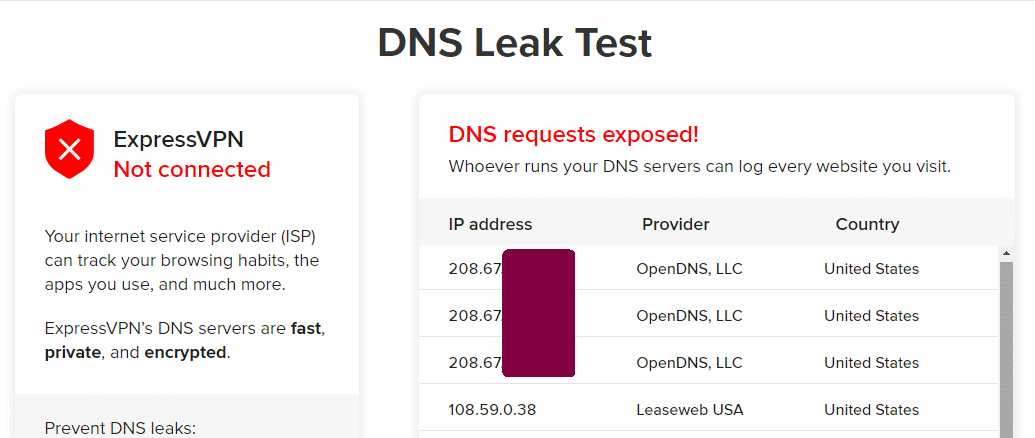
Limited VPN tester while continued to a VPN
On Windows, the simply tester page in a higher place that has been bullet-proof in my experience is the one for OpenDNS. Information technology but reports a YES/NO on whether OpenDNS is being used and it is not fooled by whatsoever caching issue confuses the other testers. As a side note, all the VPN services I have used assign a single DNS server. Outside of a VPN, at that place are usually two or more than DNS servers in use.
Another effect is that different DNS testers report a unlike number of DNS servers. Some only report on one DNS server, others study on multiple DNS servers. I don't know why this is.
Cloudflare DNS servers are one.1.1.1 and i.0.0.1. In November 2018, Cloudflare released iOS and Android apps that configure those systems to use their DNS servers. Information technology works by creating a pseudo VPN connection. The testers above practice not study either one.one.i.1 or 1.0.0.1 as the in-utilize DNS servers. The Cloudflare app will bear witness that it is being used, and I am sure it is, just the in a higher place DNS testers report other IP addresses. And, you can't get by the hostname either, the servers used by Cloudflare do not have host names. The only clue from these testers is that Cloudflare is the Internet service provider.
Ane feature of Cloudflare DNS is encryption. The connexion between your computer and their DNS server is encrypted using one of two adequately new approaches: DNS over TLS or DNS over HTTP. This only an issue when you are not using a VPN. A VPN encrypts everything (when it is working correctly) coming and going from the computer so there is no need to pay special attention to encrypting DNS.
Warning to WIRED readers: The article Yous Know What? Go Ahead and Employ the Hotel Wi-Fi past Brian Barrett (Nov 18, 2018) comes to a very incorrect determination. The principal point of the article is that the widespread use of HTTPS (secure websites) eliminates the old dangers of sniffing and snooping on unencrypted data. For one affair, this shows a lack of understanding of the limits of HTTPS. Secure websites do not deserve that much trust. Still, the bigger danger is that on a public wireless network yous have an encrypted connection to bad guys. HTTPS does nada to protect you lot from a scam website that looks real enough, displays the correct URL in the accost bar, merely whose sole purpose is to harvest passwords. Extended Validation could offer this protection, but in the real world it does not. For one thing, web browsers are constantly changing how they signal EV vs. DV (Domain Validation). And, some browsers do not requite any visual indication of the difference. And, I doubtable no not-techies are even aware of the EV/DV concept in the offset place. Even more insidious is using DNS not to false out the main/displayed domain proper noun, but to signal the browser at a scam copy of included code from a 3rd party. Many sites are compromised by including malicious code from hacked 3rd parties. DNS means that the third party does non even need to be hacked. So, using trustworthy DNS servers, not those from hackers, a coffee shop or a hotel, is critical to computing safely. The article too ignores the event of evil twin networks, an assault for which at that place is (as far as I know) no defence.
Anyone running a VPN on Windows viii or 10 needs to exist aware of a situation where DNS requests may be sent outside of the VPN tunnel. For more, run into Guide: Prevent DNS leakage while using a VPN on Windows 10 (and Windows 8).
In May 2017, Trend Micro made a not bad signal: "Unfortunately, website-based tests may not exist reliable once a home router has been compromised." With that in mind, information technology makes sense to check with the router direct, be information technology with a web interface or an app, to double check the DNS servers.
Windows users have another first-class option, the DNS query sniffer program by Nir Sofer. The program is complimentary, portable and from a trustworthy source. Information technology merely traces DNS requests and responses. Before connecting to a VPN, tell it to examine either your Wi-Fi or Ethernet connection to confirm the plan is working. And then connect to the VPN and you should see no further DNS activity. As further proof that the VPN is handling things, tell the plan to examine your VPN connectedness (Options -> Capture Options) and you lot should see all your DNS requests.
Every bit for whether a DNS server is actually working well, we take Steve Gibson's a DNS spoofability examination. The page has no creation date and no last update date, but it has been around for a long time.
Page Created: Nov 13, 2018
Last Updated: March 17, 2022 5PM CT
Viewed 744,481 times
(570/day over 1,305 days)
Copyright 2015 - 2022
Source: https://routersecurity.org/testdns.php
Posted by: cobbposis1961.blogspot.com

0 Response to "How Do I Find My Dns Server?"
Post a Comment